Every quarter, we publish compliance and security insights that you can share with your employees to fulfill periodic security reminder requirements your organization may be subject to.
As an added bonus, we’ve highlighted some developing security trends and featured a quick tip to get more out of your compliance management.
Use a Compliance Management System for Greater Data Continuity
Your organization needs to be able to recover from data loss events, and there are multiple ways that data loss can occur. One of those ways is for knowledge experts to leave their position or leave the organization altogether. When Emily is no longer in her role, all of her expertise and historical knowledge leaves with her.
As turnover occurs year over year, there’s a certain lack of continuity with your annual compliance engagement. This change means that other personnel need to learn new things (that Emily had all figured out) to cover the gap. That introduces new inefficiencies and increased risk for the organization as you’re transitioning new personnel who have responsibilities for the company’s security posture.
If your company doesn’t have a compliance management system that automatically consolidates all of your data and historical records into a single location, it amplifies the pain your organization goes through as you try to make up for those staffing transitions every year.
(It’s also the responsibility of your organization to enforce the compliance management system as the single point of truth for compliance-related evidence for the company. Don’t allow evidence to flow through multiple channels, such as email, text, file servers or file sharing sites.)
This is one of the reasons why we recommend that every organization uses some form of a quality compliance management system as the single source of truth. If you’re stuck in the mire of spreadsheets or hunting down evidence submissions across multiple channels, you’re burning hundreds of wasted hours — and throwing away thousands of dollars in operational costs.
With an efficient compliance management system, you have a rock-solid repository with a historical record of how evidence was collected and submitted in previous years. So, new personnel can refer to the activities of their predecessor to learn quickly and contribute meaningfully right out of the gate. There’s less wasted time and quicker evidence submission from your whole team.
Since you have a single source of truth, with historical records at your fingertips, you know beyond a shadow of a doubt what evidence passed muster with the Assessor last year. Which means it’s quick and easy to submit the right evidence this time around.
TCT Portal Quick Tip: Introducing EZ Cert for TCT Portal
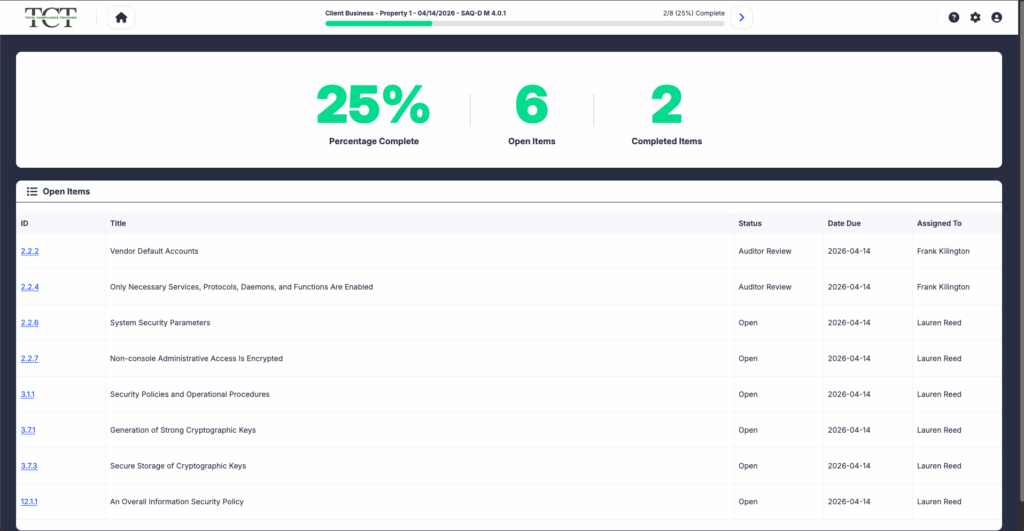
TCT Portal has just gotten easier than ever to use — especially if you aren’t a highly technical “gearhead.”
Most of our users have deep technical knowledge and need a compliance tool that deals with all of the complexities of compliance management. But most organizations rely on non-technical users to submit evidence as well. For these users, the full-featured interfaces in TCT Portal can be a bit overwhelming.
That’s why we’ve just released EZ Cert for TCT Portal. EZ Cert is a simplified interface that allows non-technical users to see only the controls they need to use. It’s a modernized, easy-to-use dashboard that feels familiar and intuitive for these contributors.
EZ Cert is specifically designed to reduce friction, eliminate confusion, and cut through the complexity of evidence submission for business leaders, control owners, and personnel involved in supporting compliance evidence provisioning.
The interface presents each assigned user with a clear, intuitive pathway to only the tasks that require their attention. There’s no clutter, no extraneous navigation, and no risk of getting lost in the forest of the overall compliance controls for the organization. Occasional users can confidently and quickly engage in compliance activities, without the anxiety of navigating an interface designed to support gearheads, advanced administrators, Consultants, and Assessors.
EZ Cert is currently available to all TCT Portal customers. Learn more about EZ Cert, or contact Portal Support to discuss deploying it at your organization.
What’s Going on in Security Today
Google Patches Gemini AI Hacks Involving Poisoned Logs, Search Results
Google has patched some recently discovered Gemini AI hacks involving poisoned logs and search results. Attackers could send specially crafted requests to a target organization through Gemini. When completed, it would add a malicious prompt to that organization’s log file.
Akira ransomware: From SonicWall VPN login to encryption in under four hours
Akira ransomware affiliates claim they can bypass SonicWALL credentials and MFA within four hours. They laid out the steps, in the correct order, on how to get inside SonicWALLs. Arctic Wolf is reporting an increase in Akira-like attacks. It appears to be related to a zero-day exploit in SonicWALL VPN devices. There was an improper access control vulnerability in SonicWALL 6, which was patched in version 7. Unfortunately, most companies did not reset the passwords for the users logging into the VPN service, so the accounts were still able to be exploited.
AI-Powered Voice Cloning Raises Vishing Risks
There is a new type of phone scam causing major concerns because it is rapidly gaining steam. Vishing risks are on the rise. AI, with only about five minutes of a recorded voice sample, can recreate a victim’s voice. Attackers pose as the victim and gain personal information from a call, while trying to prolong the call and continuing to extract information from the targeted person. This attack vector underscores the need to validate phone calls through a secondary channel.
CISA Sounds Alarm on Critical Sudo Flaw Actively Exploited in Linux and Unix Systems
There is a new flaw in Linux and Unix systems that is impacting the sudo command utility. This flaw could allow a local attacker to leverage Sudo’s -R option, allowing them to run arbitrary commands as root, even without being in the sudoers file. This is why physical security and connection methods to corporate networks are more important than ever.
New Android Trojan “Datzbro” Tricking Elderly with AI-Generated Facebook Travel Events
There is a new Android-based Trojan malware called Datzbro that is designed to target elderly phone users. Fake websites tell the elderly who are looking for social activities, trips, in-person meetings and more, advising them to download the “community application.” A wide range of capabilities are available, once deployed, including a placeholder link for an iOS application using TestFlight.
DPRK Hackers Use ClickFix to Deliver BeaverTail Malware in Crypto Job Scams
North Korean hackers have been leveraging ClickFix lures to deliver a malware known as BeaverTail/InvisibleFerret. BeaverTail is delivered via social engineering in a cluster of activities called ClickFake Interviews. Once in, they use a fake videoconference software like FCCCall or FreeConference to install a backdoor called InvisibleFerret. The newest vector is advertising as a Web3 organization trying to get targets to invest in Web3 companies, as well as offering fake jobs in crypto trading, sales, and marketing roles for these fake Web3 companies.

Get industry insider expertise delivered to your inbox
Subscribe to the TCT blog